What is ModSecurity?
ModSecurity is a free and open source web application that started out as an Apache module and grew to a fully-fledged web application firewall. It works by inspecting requests sent to the web server in real time against a predefined rule set, preventing typical web application attacks like XSS and SQL Injection.
ModSecurity can be installed by running the following command in your terminal:
sudo apt install libapache2-mod-security2 -y
sudo a2enmod headers
sudo systemctl restart apache2
Configuring ModSecurity
ModSecurity is a firewall and therefore requires rules to function. This section shows you how to implement the OWASP Core Rule Set. First, you must prepare the ModSecurity configuration file.
Remove the .recommended extension from the ModSecurity configuration file name with the following command:
sudo cp /etc/modsecurity/modsecurity.conf-recommended /etc/modsecurity/modsecurity.conf
SecRuleEngine On
File: /etc/modsecurity/modsecurity.conf
# -- Rule engine initialization ----------------------------------------------
# Enable ModSecurity, attaching it to every transaction. Use detection
# only to start with, because that minimises the chances of post-installation
# disruption.
#
SecRuleEngine On
...
Restart Apache to apply the changes:
sudo systemctl restart apache2
Setting Up the OWASP ModSecurity Core Rule Set
First, delete the current rule set that comes prepackaged with ModSecurity by running the following command:
sudo rm -rf /usr/share/modsecurity-crs
sudo apt install git
sudo git clone https://github.com/coreruleset/coreruleset /usr/share/modsecurity-crs
sudo mv /usr/share/modsecurity-crs/crs-setup.conf.example /usr/share/modsecurity-crs/crs-setup.conf
sudo mv /usr/share/modsecurity-crs/rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf.example /usr/share/modsecurity-crs/rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf
Enabling ModSecurity in Apache 2
To begin using ModSecurity, enable it in the Apache configuration file by following the steps outlined below:
Using a text editor such as vim, edit the /etc/apache2/mods-available/security2.conf file to include the OWASP-CRS files you have downloaded:
File: /etc/apache2/mods-available/security2.conf
<IfModule security2_module>
SecDataDir /var/cache/modsecurity
Include /usr/share/modsecurity-crs/crs-setup.conf
Include /usr/share/modsecurity-crs/rules/*.conf
</IfModule>
In /etc/apache2/sites-enabled/000-default.conf file VirtualHost block, include the SecRuleEngine directive set to On.
File: /etc/apache2/sites-enabled/000-default.conf
<VirtualHost *:80>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
SecRuleEngine On
</VirtualHost>
sudo systemctl restart apache2
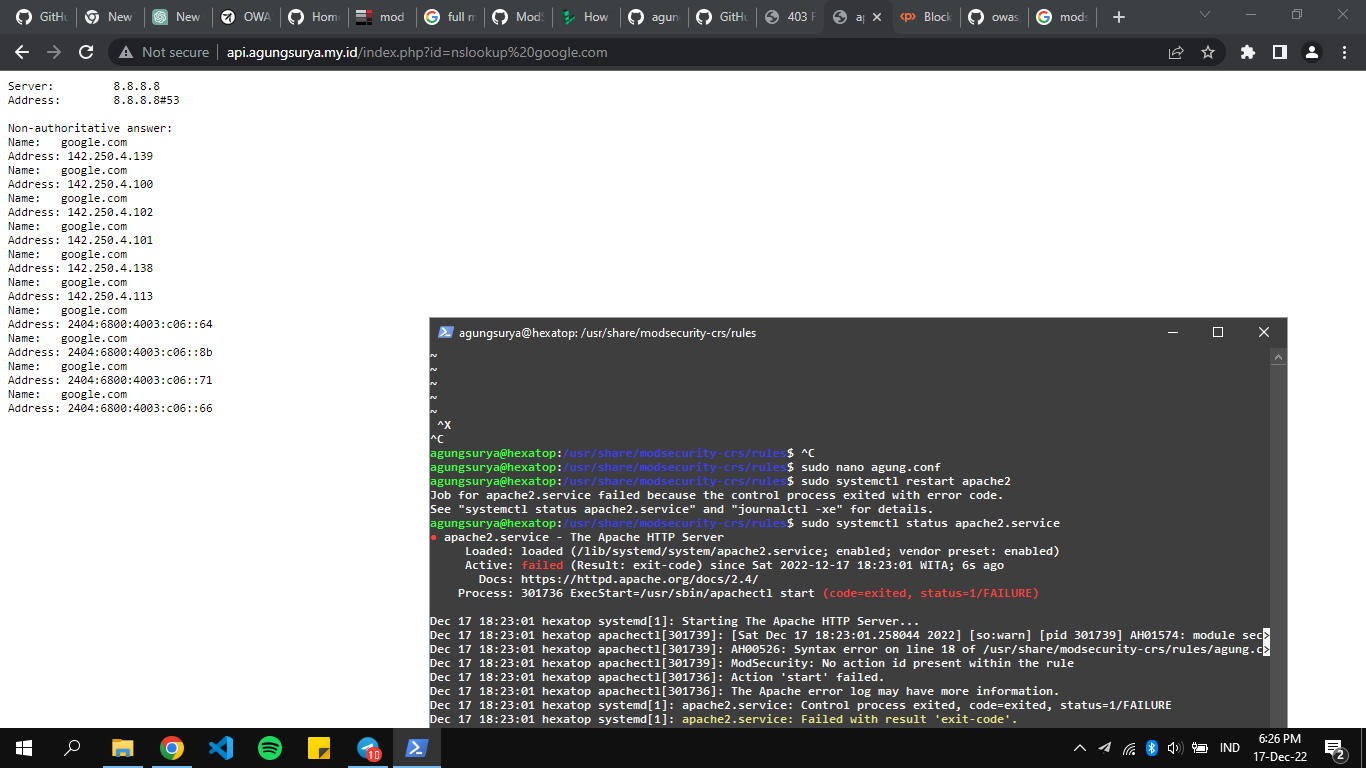
Testing ModSecurity
sebelum
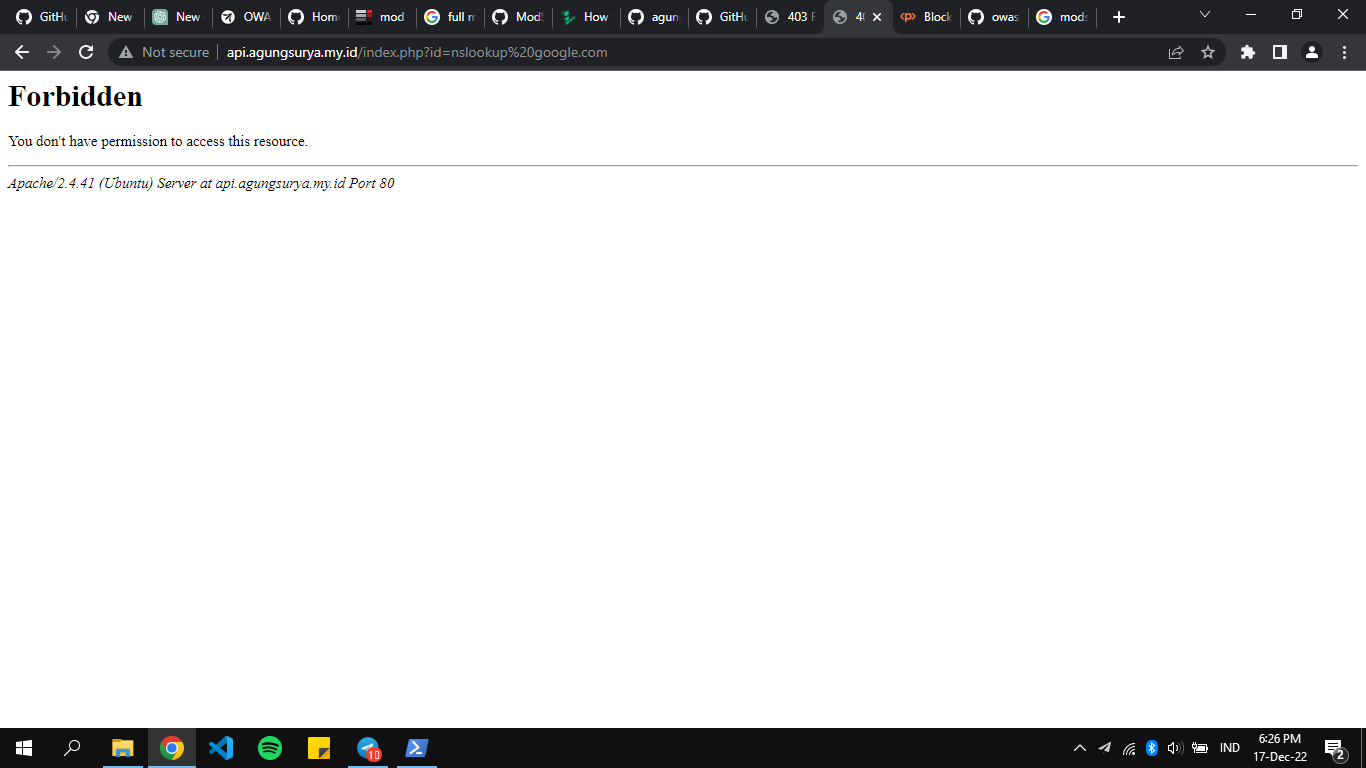
sesudah
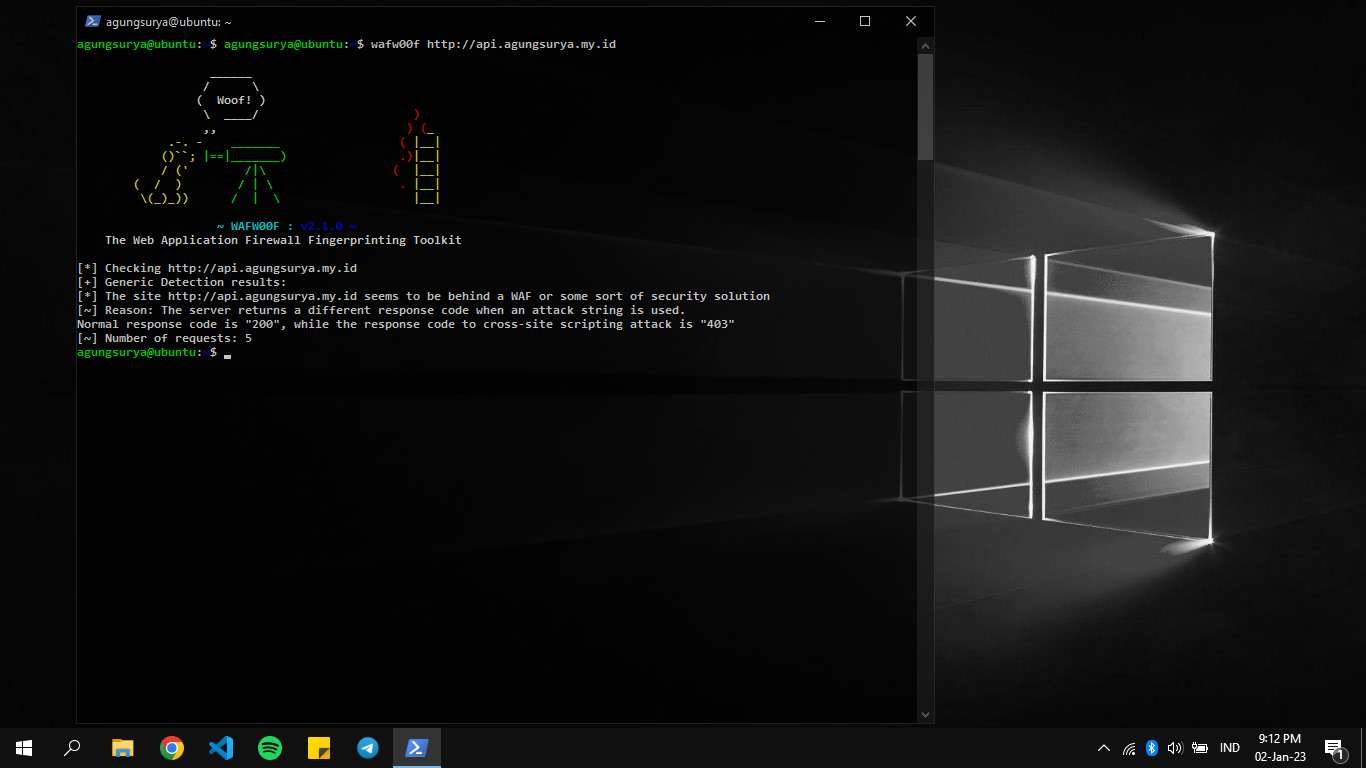
wafw00f (Web Application Firewall Detection Tool)
Wafw00f adalah singkatan dari "Web Application Firewall Detection Tool". Ini adalah alat open-source yang digunakan untuk mendeteksi jenis firewall aplikasi web yang digunakan pada server web. Alat ini bekerja dengan mengirimkan serangkaian permintaan ke server web dan menganalisis respons yang diterima. Wafw00f dapat mengenali sejumlah besar firewall aplikasi web, termasuk ModSecurity, Akamai, F5 BIG-IP, Cloudflare, Barracuda, dan banyak lagi. Dengan menggunakan wafw00f, pengguna dapat menentukan apakah suatu situs web dilindungi oleh firewall aplikasi web, dan jika ya, jenis firewall apa yang digunakan. Hal ini dapat membantu pengguna untuk mengidentifikasi potensi kelemahan dalam konfigurasi firewall dan mengambil tindakan yang diperlukan untuk meningkatkan keamanan situs web mereka.
pengunaan tools wafw00f
curl http://<SERVER-IP/DOMAIN>/index.php?exec=/bin/bash
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>403 Forbidden</title>
</head><body>
<h1>Forbidden</h1>
<p>You don't have permission to access this resource.</p>
<hr>
<address>Apache/2.4.25 (Debian) Server at 96.126.105.75 Port 80</address>
</body></html>
ModSecurity
